Cybersecurity
Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. Also known as information technology (IT) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization.
In 2020, the average cost of a data breach was USD 3.86 million globally, and USD 8.64 million in the United States. These costs include the expenses of discovering and responding to the breach, the cost of downtime and lost [1] revenue, and the long-term reputational damage to a business and its brand. Cybercriminals target customers’ personally identifiable information (PII) - names, addresses, national identification numbers (e.g., Social Security numbers in the U.S., fiscal codes in Italy), credit card information - and then sell these records in underground digital marketplaces. Compromised PII often leads to a loss of customer trust, regulatory fines, and even legal action.
Security system complexity, created by disparate technologies and a lack of in-house expertise, can amplify these costs. But organizations with a comprehensive cybersecurity strategy, governed by best practices and automated using advanced analytics, artificial intelligence (AI) and machine learning, can fight cyberthreats more effectively and reduce the lifecycle and impact of breaches when they occur.
Cybersecurity Domains
A strong cybersecurity strategy has layers of protection to defend against cyber crime, including cyber attacks that attempt to access, change, or destroy data; extort money from users or the organization; or aim to disrupt normal business operations. Countermeasures should address:
- Critical infrastructure security -practices for protecting the computer systems, networks, and other assets that society relies upon for national security, economic health, and/or public safety. The National Institute of Standards and Technology (NIST) has created a cybersecurity framework [2] to help organizations in this area, while the U.S. Department of Homeland Security (DHS) provides additional guidance.
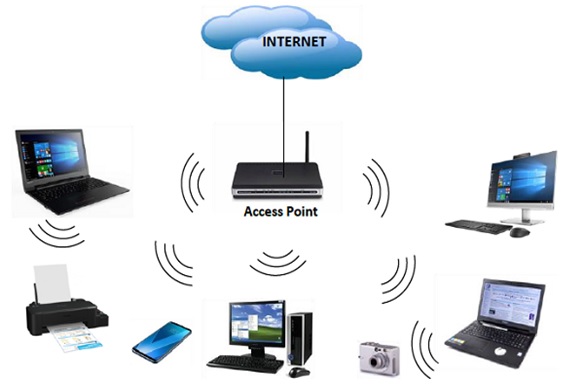
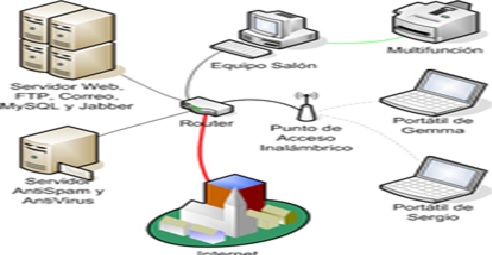
- Network security -security measures for protecting a computer network from intruders, including both wired and wireless (Wi-Fi)connections.
- Application security - processes that help protect applications operating on-premises and in the cloud. Security should be built into applications at the design stage, with considerations for how data is handled, user authentication, etc.
- Cloud security -specifically, true confidential computing that encrypts cloud data at rest (in storage), in motion (as it travels to, from and within the cloud) and in use (during processing) to support customer privacy, business requirements and regulatory compliancestandards.
- Information security -- data protection measures, such as the General Data Protection Regulation or GDPR, that secure your most sensitive data from unauthorized access, export.
- End-user education -building security awareness across the organization to strengthen endpoint security. For example, users can be trained to delete suspicious email attachments, avoid using unknown USB devices, etc.
- Disaster recovery / business continuity planning -tools and procedures for responding to unplanned events, such as natural disasters, power outages, or cybersecurity incidents, with minimal disruption to key operations.
cybersecurity myths
The volume of cybersecurity incidents is on the rise across the globe, but misconceptions continue to persist, including the notion that:
Cybercriminals are outsiders. In reality, cybersecurity breaches are often the result of malicious insiders, working for themselves or in concert with outside hackers. These insiders can be a part of well-organized groups, backed by nation-states.
Risks are well-known. In fact, the risk surface is still expanding, with thousands of new vulnerabilities being reported in old and new applications and devices. And opportunities for human error - specifically by negligent employees or contractors who unintentionally cause a data breach - keep increasing.
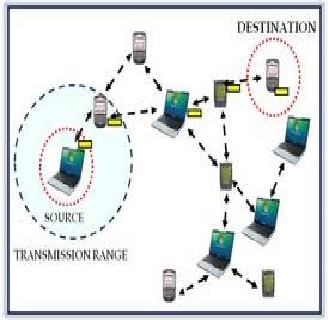
Attack vectors are contained. Cybercriminals are finding new attack vectors all the time - including Linux systems, operational technology (OT), Internet of Things (IoT) devices, and cloud environments.
My industry is safe. Every industry has its share of cybersecurity risks, with cyber adversaries exploiting the necessities of communication networks within almost every government and private-sector organization. For example [3], ransomware attacks (see below) are targeting more sectors than ever, including local governments and non-profits, and threats on supply chains, ".gov" websites, and critical infrastructure have also increased figure1.
Essential Functions of a Cybersecurity Program
- Security Operations Center (SOC)
- Security Information and Event Management (SIEM)
- Staffing Your SOC
- Business Planning
- Cybersecurity Project Support
- Security and Regulatory Compliance
- Security Administration
- Cyber Risk Management [4]

Figure1: cyber security
Types of cyber security
- Critical infrastructure security: Critical infrastructure security consists of the cyber-physical systems that modern societies rely on. ... [5]
- Application security: You should choose application security as one of the several must-have security measures adopted to protect your systems.
- Network security: As cyber security is concerned with outside threats, network security guards against unauthorized intrusion of your internal networks due to malicious intent.
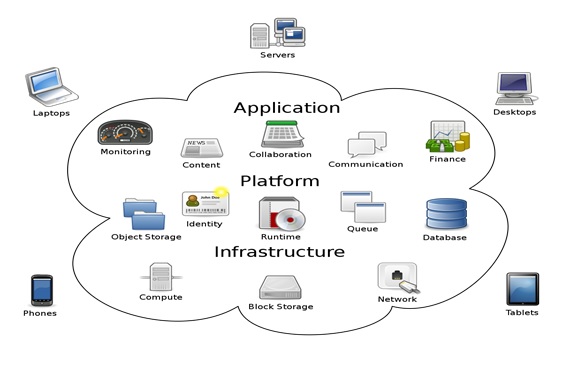
- Cloud security: Improved cyber security is one of the main reasons why the cloud is taking over.
- Internet of things (IoT) security
References:
- https://www.ibm.com/topics/cybersecurity
- https://www.javatpoint.com/what-is-cyber-security
- https://intellipaat.com/blog/what-is-cyber-security
- www.cyberriskopportunities.com/essential-functions-of-a-cybersecurity-program
- mind-core.com/blogs/cybersecurity/5-types-of-cyber-security
Cite this article:
S. Nandhinidwaraka (2021), Cybersecurity, AnaTechMaz, pp. 11