The Future of Encryption
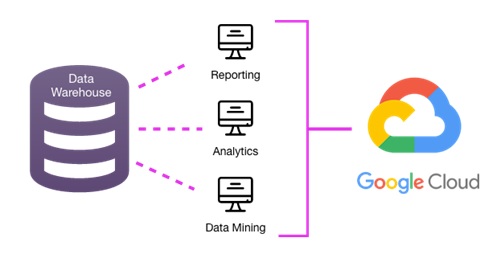
Data encryption is the process by which digital data is translated into a complex code using encryption algorithms. This code can only be read, encrypted, or decrypted if you have the decryption key. Organizations use data encryption to ensure the secure transmission of storage of private or confidential digital data. The purpose of data encryption goes beyond secure storage and transmission of your data; it includes message authentication and integrity that verify the message’s origin and that it was not changed since being sent. Authentication and digital signatures provide an additional layer of data security for sensitive data.[1]
Figure 1. The future of encryption in world
Figure 1 shows today’s federal agencies are generating, analyzing, and transporting data at an unprecedented, exponentially accelerating rate. To keep all that data safe—whether it’s at rest, in use, or on the move—the government must not only employ today’s most reliable encryption technologies, it must be ready to adopt tomorrow’s as well. As insider and adversarial threats grow and advance, promising new approaches to encryption—like post-quantum cryptography, quantum key distribution, and homomorphic encryption—will be key to maintaining the nation’s information security.[2]
The Future of Encryption
Now that we have a clearer understanding of what data encryption means for you, let’s get into some of the development in cryptography we’re most excited for in the future.
1. Quantum Cryptography
Quantum cryptography uses photons of light and the principles of quantum physics to physically move data between a sender and recipient. Because information is transmitted using light, it cannot be intercepted, copied, or cloned. With the help of quantum mechanics, it can be sent so that only the intended recipient is able to read it without the data being altered. No additional level of encryption would be necessary because the data would be useless if it were to be intercepted by anyone other than the recipient.
2. Honey Encryption
Honey encryption is a bit of a misnomer in that it doesn’t rely on traditional encryption approaches. Instead, it deters cybercriminals by making them think they’ve gained access to your network or data when, in reality, they have only obtained false or irrelevant data.
3. Facial Recognition Encryption
We’re already beginning to witness the foundations being laid for facial encryption. As facial recognition technology advances, we expect to see facial encryption become a fundamental way of securing data and protecting access to confidential information.
4. Homomorphic Encryption
Traditional encryption approaches create a point of vulnerability when you encrypt a message and again when you decrypt it even with a private key. Unfortunately, we have to decode data in order to access and use it. Homomorphic encryption seeks to tackle this problem by allowing you to use and access encrypted data without ever having to decrypt it in the first place.[1]
Today, modern encryption uses 'keys' to safeguard data on our computers, mobile devices, and communication networks. Encryption converts data into digital gibberish, so it can't be used maliciously. If the message recipient has the right keys, then the data can be decrypted for processing by a computer or mobile device.[3]
References:
- https://reverus.com/the-future-of-encryption/
- https://www.boozallen.com/s/insight/publication/the-future-of-encryption.html
- https://sciencenode.org/feature/the-future-of-encryption.php
Cite this article:
Thanusri swetha J (2021), The Future of encryption, Anatechmaz, pp. 25