- Home
- Future Technologies
- Networking
-
Next-Generation Hotspot (NGH)
By : Gokula Nandhini K, NGH provides users with an “Always on” Wi-Fi experience, upgrading the network security with enhanced authentication and encryption via WPA2/WPA3 enterprise security...
-
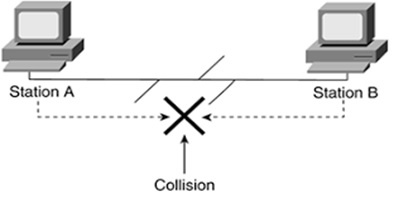
Carrier sense multiple access with collision detection (CSMA/CD)
By : Gokula Nandhini K, Carrier sense multiple access with collision detection (CSMA/CD) is the opposite of CSMA/CA. Instead of detecting data to transmit...
-
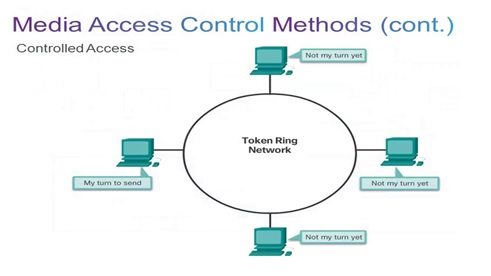
Methods of Media Access Control
By : Janani R, In this manner, the point in these networks is to have the option to use the transmission capacity effectively, and ensure decency to all nodes. As we probably are aware, wireless networks...
-
Network function virtualization (NFV)
By : Gokula Nandhini K, Network functions virtualization (NFV) is the replacement of network appliance hardware with virtual machines. The virtual machines use a hypervisor to run networking software...
-
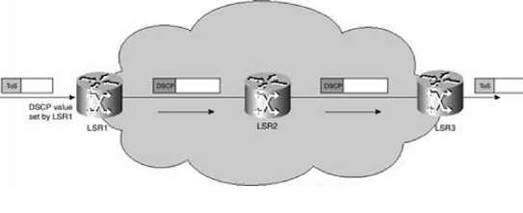
Overview of Per-Hop Behaviors
By : Gokula Nandhini K, In diffserv terminology, the forwarding behavior that is assigned to a DSCP is called the per-hop behavior (PHB). The PHB defines the forwarding precedence a marked packet...
-
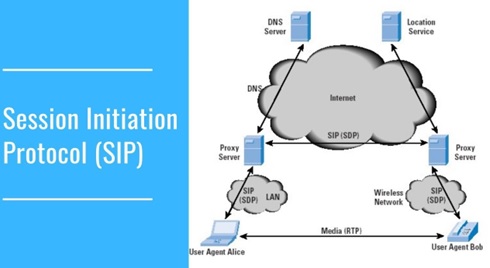
Overview of Session Initiation Protocol
By : Janani R, Session Initiation Protocol (SIP) is used to signal and control interactive communication sessions. The uses for such sessions include voice, video, chat and instant messaging, as well as...
-
Gigabit and 10 Gb Ethernet
By : Gokula Nandhini K, 10 gigabit Ethernet — otherwise known as 10 GbE, 10GE or 10G Ethernet — is an Ethernet technology that transmits at 10 gigabits per second. When 10gb Ethernet came...
-
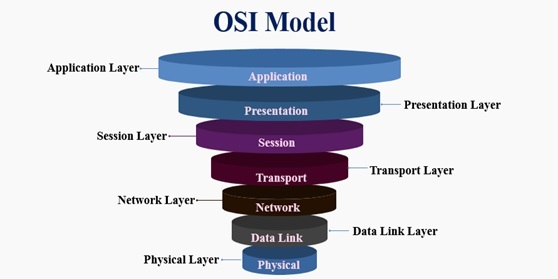
7 Layers OSI Model
By : Gokula Nandhini K, OSI stands for Open Systems Interconnection. It has been developed by ISO – ‘International Organization for Standardization‘, in the year 1984. It is a 7-layer architecture with each...
-
Dynamic Host Configuration Protocol
By : Gokula Nandhini K, DHCP (Dynamic Host Configuration Protocol) is a network management protocol used to dynamically assign an IP address to any device, or node, on a network...
-
The OSI Model
By : Gokula Nandhini K, OSI Model is a short name for the Open Systems Interconnection reference model for networking. This theoretical model explains how networks behave within an orderly...
-
Bandwidth Management
By : Hana M, Bandwidth management is the process of controlling and optimizing the amount of data that can be transmitted over a network, in order to ensure that critical applications and services receive...
-
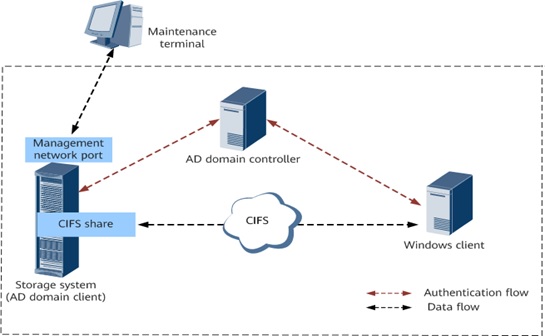
Common Internet File System (CIFS)
By : Hana M, The Common Internet File System (CIFS), also known as Server Message Block (SMB), is a file sharing protocol that enables remote clients to access files and printers on a server over a network...
-
Data Loss Prevention (DLP)
By : Hana M, Data Loss Prevention (DLP) is a set of security measures and technologies that are designed to prevent the unauthorized disclosure, leakage, or loss of sensitive data. DLP solutions are used...
-
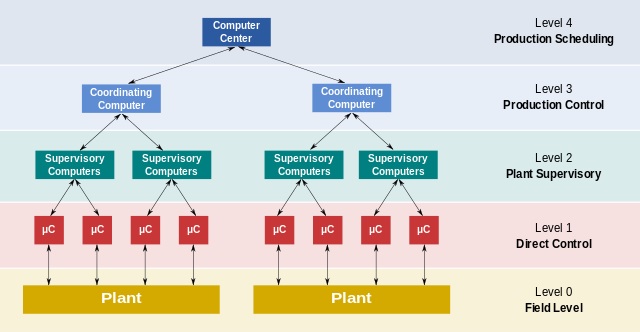
Distributed Control Systems (DCS)
By : Hana M, A Distributed Control System (DCS) is a specialized control system used to manage and automate complex industrial processes. DCS is made up of a network of distributed computing...
-
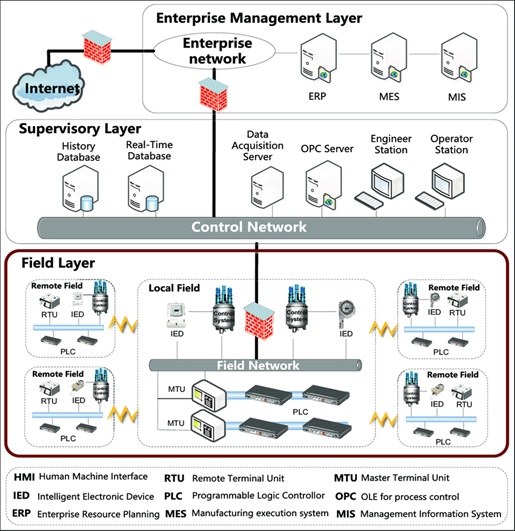
Industrial Control Systems (ICS)
By : Hana M, Industrial Control Systems (ICS) are specialized control systems used to manage and automate industrial processes, such as manufacturing, energy generation, and transportation systems...