- Home
- Future Technologies
- Networking
-
New Method Allows for Faster Detection of Ransomware
By : Thanusri swetha J, Ransomware is malware that uses encryption to hold a victim’s data hostage. The critical data of a user or organization is encrypted so that they cannot access files, databases...
-
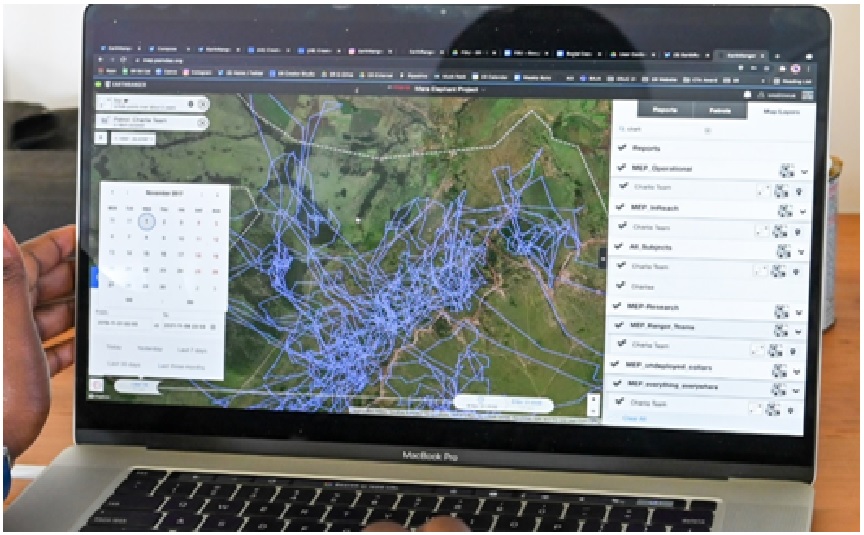
Code-free conservation
By : Thanusri swetha J, Due to high-tech, low-cost monitoring gadgets, the research of wildlife motion is having its Massive Knowledge second. However to this point, solely individuals with knowledge...
-
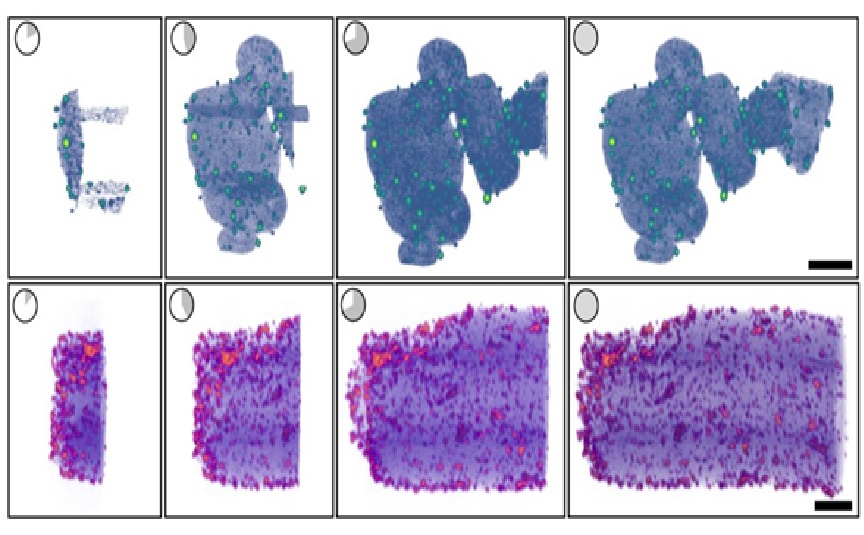
Open-source software enables researchers to visualize nanoscale structures in real time
By : Thanusri swetha J, Computer chip designers, materials scientists, biologists and other scientists now have an unprecedented level of access to the world...
-
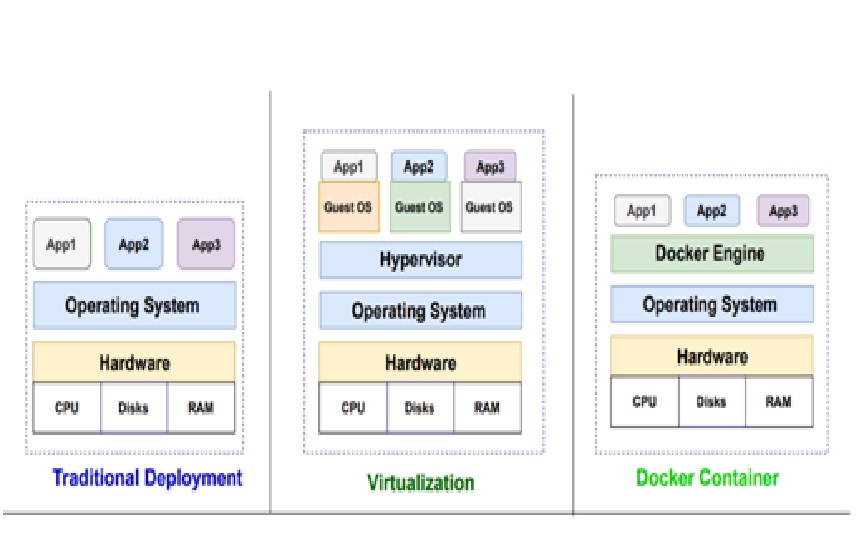
Overview of containerization
By : Thanusri swetha J, While virtualization is a general strategy for getting more out of in-house hardware resources, containerization is a specific type of hardware virtualization. Containerization...
-
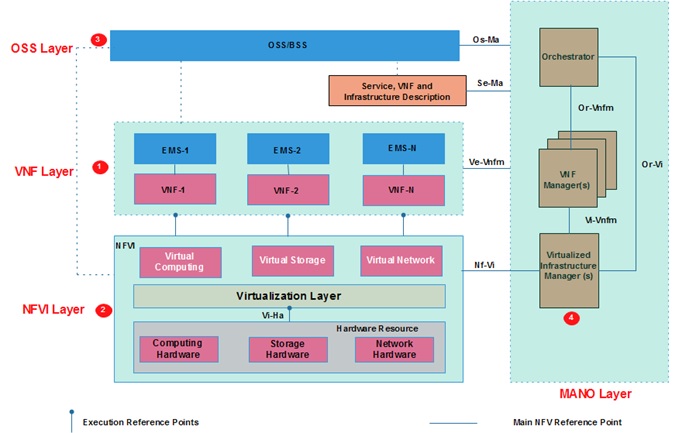
Network Function Virtualization (NFV)
By : Hana M, The term “Network Functions Virtualization” (NFV) refers to the use of virtual machines in place of physical network appliances. There is a requirement for a hypervisor...
-
5G and Wi-Fi 6G Technology
By : Janani R, 5G or fifth generation cellular technology. It is characterized by increased speed, reduced latency and improve flexibility in wireless services. It helps organizations to mobilize...
-
Cyber security
By : Janani R, Cybersecurity is the practice of protecting computer systems, networks, and sensitive information from theft, damage, or unauthorized access. With the increasing reliance on technology...
-
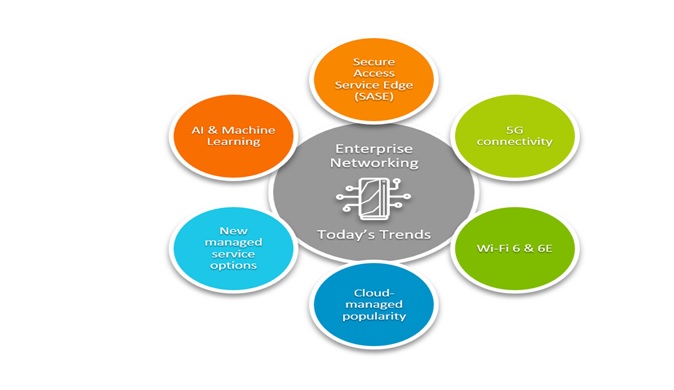
Enterprise Network Strategy
By : Gokula Nandhini K, The COVID-19 pandemic and changing workforce expectations have led many companies to a more globally distributed remote workforce. As a result, enterprise networking...
-
Networking with remote AI support
By : Gokula Nandhini K, Users and enterprise devices often need technical support that was normally provided in the office. As remote work continues to become a standard approach, many companies...
-
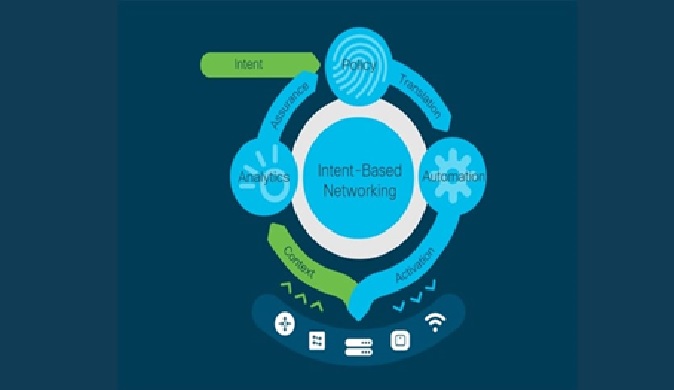
The Growth Of Intent-Based Networking (IBN)
By : Gokula Nandhini K, Networking technology continues to grow more sophisticated. Particularly with the more widespread use of software-defined networking (SDN), intent-based networking...
-
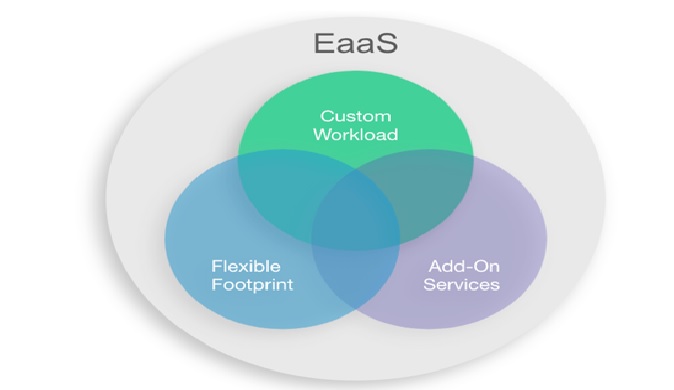
Edge-as-a-Service (EaaS)
By : Gokula Nandhini K, A large portion of applications, particularly enterprise apps, leverage a heterogeneous network of public clouds, private clouds, on-premise data centers, and edge. A shift toward this kind...
-
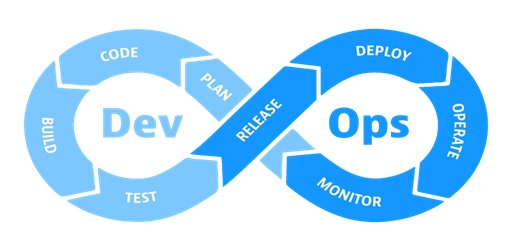
DevOps in Network
By : Gokula Nandhini K, DevOps is tied up to software development and IT. DevOps improve relationship between network service designers and engineers to make operational changes to the services...
-
Data Security Posture Management
By : Gokula Nandhini K, Data Security Posture Management (DSPM) defines a new, data-first approach to securing cloud data. DSPM is based on the premise that data is your organization’s...
-
Digital transformation
By : Gokula Nandhini K, It enables adoption of digital technology to transform services or businesses, by replacing on digital or manual processes with digital processes. Process of digitization transforms...
-
Multi-cloud networking software
By : Gokula Nandhini K, Multi-cloud networking software (MCNS) addresses the challenges related to connecting networks and applications across multiple public cloud environments. MCNS products...