Data Leakage Detection System
A Data Leakage Detection System is a security mechanism designed to identify, monitor, and prevent the unauthorized transmission of sensitive data from an organization's internal systems to external entities. It helps protect confidential information such as personal data, intellectual property, financial records, and trade secrets from being leaked—either accidentally or maliciously.
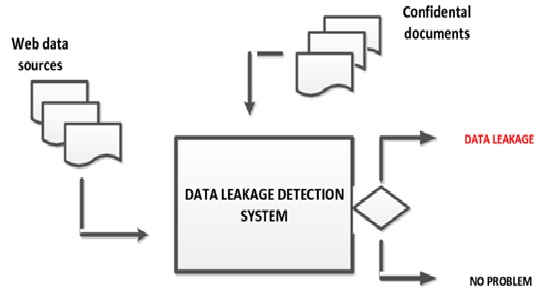
Figure 1. Smart System for Detecting and Preventing Data Leaks.
Introduction to Data Leakage
What is Data Leakage?
Data leakage refers to the unintended or unauthorized transfer of sensitive data from an organization to external parties. This data can include customer information, financial records, intellectual property, or confidential internal documents. Figure 1 shows Smart System for Detecting and Preventing Data Leaks.
Causes of Data Leakage:
- Accidental sharing (e.g., misdirected emails)
- Insider threats (malicious employees)
- Weak security policies
- Malware or phishing attacks
Identifying and Classifying Sensitive Data
Before a system can detect leaks, it must understand what qualifies as sensitive data.
Data Discovery:
The system scans databases, email servers, user devices, and cloud platforms to locate sensitive files.
Data Classification:
- Public: No restrictions (e.g., marketing brochures)
- Internal Use Only: Not to be shared outside the organization
- Confidential: Includes customer data, internal plans, etc.
- Highly Confidential: Financial records, trade secrets, legal documents
Monitoring and Detecting Data Leakage
Channels Where Leaks Can Occur:
- Email and messaging platforms (e.g., Slack, Teams)
- Cloud storage (e.g., Google Drive, Dropbox)
- USB drives and removable media
- Printing and screenshots
- Web uploads and social media
Detection Techniques:
- Data Loss Prevention (DLP) tools scan and block suspicious data movements.
- User Behavior Analytics (UBA) flags anomalies (e.g., sudden data downloads).
- Watermarking embeds invisible tags in documents for traceability.
- Honeytokens are fake data planted to catch malicious access.
Real-World Applications and Compliance
Who Uses It?
- Healthcare: To protect patient records (HIPAA)
- Finance: To secure account data (PCI-DSS)
- Education: For safeguarding student and staff data
- Technology Firms: To guard intellectual property and source code
benefits:
- Ensures regulatory compliance
- Detects insider threats early
- Reduces risk of legal fines
- Enhances brand reputation and customer trust
Reference:
- https://www.upguard.com/blog/how-to-detect-and-prevent-data-leakage
Cite this article:
Thanusri swetha J (2021), Data Leakage Detection System, AnaTechMaz, pp. 37