- Home
- Future Technologies
- Cloud Computing
-
Cloud security and privacy
By : Janani R, The synergy between Cloud and IoT has emerged largely due to the Cloud having attributes which directly benefit IoT and enable its continued growth. IoT adopting Cloud services has brought...
-
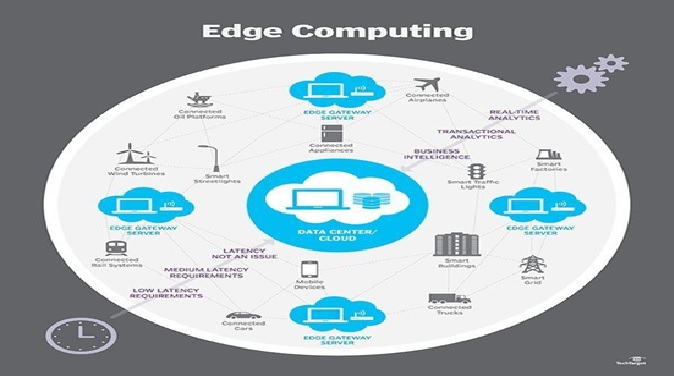
Deploying to the Edge
By : Gokula Nandhini K, Edge computing is the deployment of computing and storage resources at the location where data is produced. This ideally puts compute and storage at the same point...
-
Low-code and no-code cloud services
By : Gokula Nandhini K, Low-code platforms for cloud development allow citizen developers to produce sophisticated cloud applications and systems. Such platforms practice a visual approach...
-
Cloud Cost Optimization
By : Gokula Nandhini K, Cloud users are growing rapidly and hence managing costs has become a major concern for businesses. As a result, Cloud providers are investing in developing new tools and services...
-
Cloud Cost Optimization
By : Gokula Nandhini K, Cloud providers are investing in green computing initiatives, such as renewable energy and energy-efficient infrastructure, to reduce their carbon footprint and meet sustainability goals...
-
Kubernetes
By : Janani R, The key trend is the increased adoption of container orchestration platforms like Kubernetes and Docker. This technology enables large-scale deployments that are highly scalable and efficient...
-
Multi-cloud strategy
By : Janani R, In the past decade cloud computing has skyrocketed. What began as a limited set of computing services offered by an online retailer has become a highly sophisticated computing ecosystem...
-
Serverless Computing
By : Janani R, Serverless Computing came into the computing industry as a result of the emergence of the sharing economy. Here, compute resources are provided as a service rather than installed...
-
Avoiding Vendor Lock-In
By : Gokula Nandhini K, Vendor lock-in is the common term for a situation where an organization wishes to transfer its business away from one of its current vendors but is unable to do so due...
-
Geographic Diversity
By : Gokula Nandhini K, Geographic diversity means the degree to which a facility is physically separated from other electric generating resources supplying electricity to a utility in order to reduce...
-
Scalability and High Availability
By : Janani R, Kubernetes allows you to scale your applications up or down based on demand, ensuring that your application can handle a high volume of traffic. It also provides high availability...
-
Hosting Apps and Services at The Edge
By : Gokula Nandhini K, This year, I expect to see more cross-border businesses with distributed user bases begin to host latency-intensive apps and services at the edge of the network...
-
Mobile Cloud Computing
By : Gokula Nandhini K, In mobile cloud computing, the mobile is the console and storage and processing of the data takes outside of it. It is one of the leading Cloud Computing research topics....
-
Securing The Perimeter (DSPM)
By : Gokula Nandhini K, Perimeter security refers to natural barriers or built fortifications to either keep intruders out or to keep captives contained within the area the boundary surrounds...
-
DevSecOps
By : Gokula Nandhini K, In defining DevSecOps, we need to begin by reacquainting ourselves with what DevOps is in the first place. DevOps, as many of us know, is a set of practices and tools...