Cloud security and privacy
The synergy between Cloud and IoT has emerged largely due to the Cloud having attributes which directly benefit IoT and enable its continued growth. IoT adopting Cloud services has brought new security challenges. In this book chapter, we pursue two main goals: (1) to analyse the different components of Cloud computing and IoT and (2) to present security and privacy problems that these systems face. We thoroughly investigate current security and privacy preservation solutions that exist in this area, with an eye on the Industrial Internet of Things, discuss open issues and propose future directions.[1]
Cloud computing is becoming increasingly a magical solution and a widely adopted technology for delivering services over the Internet thanks to its diverse benefits, including services on demand, reducing costs, sharing, and configuring computing resources, and high services scalability and flexibility. However, with the emergence of this technology, the concept of security and privacy has become a major barrier to cloud services adoption. Indeed, many research works have been done to identify cloud security and privacy issues. It is in this context that in this paper, we will provide a new cloud security and privacy model (CSPM) into layers which can be considered by cloud providers during all the stages of cloud services building and monitoring.[2]

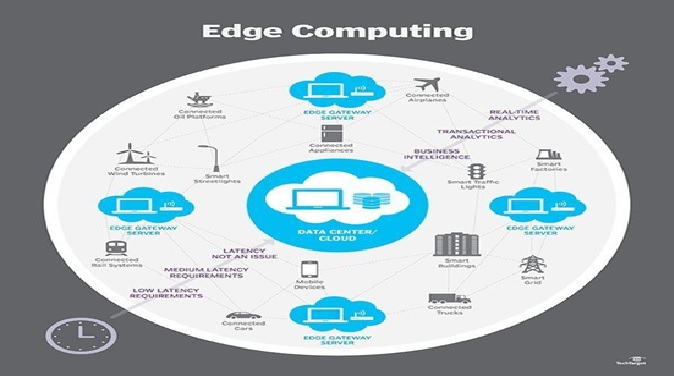
Figure .1 cloud security and privacy
Figure 1 shows Cloud security and privacy are critical concerns in the world of cloud computing.
Here are some of the key aspects that you should be aware of:
- Data protection: When you store data in the cloud, you need to ensure that it is properly protected. This includes encrypting data at rest and in transit, as well as implementing access controls and authentication mechanisms to ensure that only authorized users can access the data.
- Compliance: Depending on the type of data you store in the cloud, you may need to comply with various regulations and industry standards, such as HIPAA, GDPR, or PCI-DSS. It is essential to understand the requirements and ensure that your cloud provider meets these standards.
- Incident response: In the event of a security breach or data leak, it is crucial to have a robust incident response plan in place to minimize the impact and recover quickly. This includes regular testing and updating of the plan, as well as training employees on their roles and responsibilities in the event of an incident.
- Cloud provider selection: Not all cloud providers are created equal when it comes to security and privacy. You should carefully evaluate the security controls and certifications of potential providers and select one that aligns with your requirements and compliance obligations
- Monitoring and auditing: To maintain a secure and compliant cloud environment, you need to regularly monitor and audit the system for any suspicious activity or unauthorized access. This includes analysing logs and conducting vulnerability assessments and penetration testing.
Overall, cloud security and privacy are complex and multifaceted topics that require a proactive and comprehensive approach to ensure that your data and systems are protected.
References:
- https://link.springer.com/chapter/10.1007/978-3-319-73676-1_11
- https://ieeexplore.ieee.org/abstract/document/7847682
Cite this article:
Janani R (2023),cloud security and privacy, AnaTechMaz, pp.61