Technology of Cloud Cube Model
Cloud Cube model, helps to categorize the cloud network based on the four-dimensional factor. Their main focus is to protect and [1] secure the cloud network. This cloud cube model helps to select cloud figure 1 shown below formation for secure collaboration.
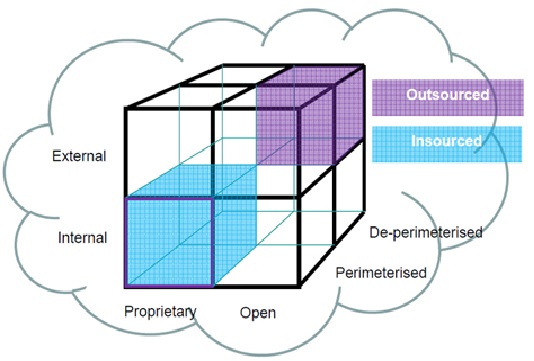
Figure 1. Cloud Cube Model
This model helps IT managers, organizations, and business leaders by providing the secure and protected network.
Security is an important concern for cloud customers and most of the cloud providers understand it. The customer should also keep in mind, the selected cloud formation meets the regulatory and location requirements.
Uses Of Cloud Cube Model
- Secondly, it ensures the information exists handiest in unique accept as true with levels.
- Thirdly, it ought to test that what regulatory compliance and regulations are relevant. For example, the information ought to live within a specific boundary and whether or not it has to live within the secure harbor or not.
- After the information classes and prepares to position withinside the required zone, the assigned man or woman can determine the subsequent elements.
- The information and processes that move withinside the cloud.
- At what stage does the consumer desire to function withinside the cloud. It may be infrastructure, platform, software program, or platform as a provider.
- The cloud formations, as in step with the requirement.
- The stage of operation withinside the cloud may be distinctive as in step with the requirement.
Internal/External: Internal/External is the most common form of the cloud. It describes the physical location of the data. It agrees [2] us whether the data exists inside or outside of your organization’s limit. In this, the data that is stored by the help of private cloud deployment will be referred to as internal, and data outside the cloud will be referred to as external.
De-perimeterized/Perimeterized: To reach de-perimeterized/perimeterized form, the user requires Jericho forum and collaboration oriented architecture commandments. It defines whether you are working inside your traditional it mindset or outside it.
The meaning Perimeterized dimension is continuing to work within the traditional it boundary, orphan signaled by network firewalls. With the support of VPN and the operation of the virtual server in your IP domain, the customer can expand the organization’s boundary into the external cloud computing domain.
Insourced/Outsourced: Insourced/outsourced is the fourth dimension of the cloud cube model. In the outsourced dimension, services are offered by the third party, and in the insourced dimension, the services are offered by the own staff. In some organizations with traditional bandwidth software or hardware, providers will run smoothly when they become cloud service providers.
Secured in the Cloud Cube Model [3]
There are various steps and point you should keep on your mind while securing your data in a cloud cube model.
- The categorization of the data, the user must know what rules must be applied to secure and protect it.
- It should make sure; that the data exist only in particular trust levels.
- It should examine that what regulatory compliance and constraints are applicable. For example: – The data must keep in a specific limit and whether it has to stay in the secure harbor or not.
>When the data is categorized and can put in the needed zone, the assigned person is in a position to decide the following aspects. - The processes and data, which are to be shift in the cloud.
- At what level the customer wants to operate in the cloud. Maybe it is infrastructure, platform, and software.
- The cloud formations, fulfill the requirements.
- In a cloud, the level of operation can be different as per the requirement.
References:
- https://data-flair.training/blogs/cloud-cube-model/
- https://difm.tech/cloud-cube-model
- https://www.tutorialandexample.com/what-is-cloud-cube-model/
Cite this article:
Nandhinidwaraka. S (2021), Technology of Cloud Cube Model, AnaTechMaz, pp. 39