The Methods of Intrusion Detection System
Intrusion detection systems are designed to identify suspicious and malicious activity through network traffic, and an intrusion detection [1] system (IDS) enables you to discover whether your network is being attacked.
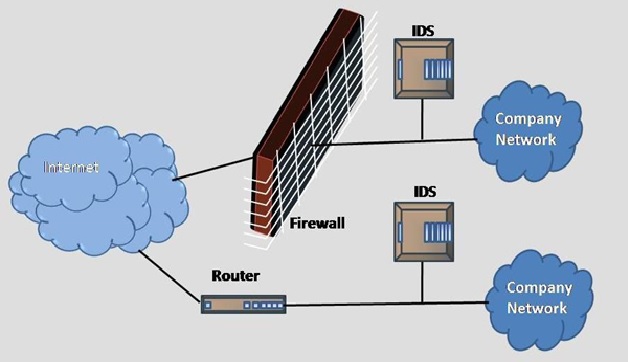
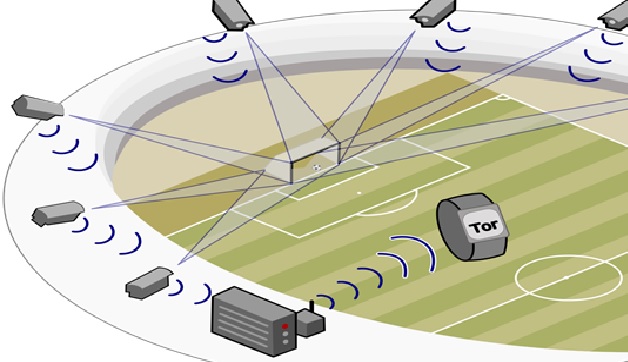
Figure 1. Intrusion Detection System
There are many great IDS options available, but in my [1] opinion SolarWinds® Security Event Manager (SEM) is a step above the rest. SEM enables real-time intrusion detection across your network and on-premises devices, and leverages many automatic capabilities designed to help optimize intrusion detection. A 30-day free trial of SEM is available.
An intrusion detection system (IDS) is software specifically built to monitor network traffic and discover irregularities. Unwarranted or unexplained network changes could indicate malicious activity at any stage, whether it be the beginnings of an attack or a full-blown breach. There are two main kinds of intrusion detection system (IDS).
A network intrusion detection [2] system (NIDS) enacts intrusion detection across your entire network, using all packet metadata and contents to determine threats.
A host-based intrusion detection system (HIDS) enacts intrusion detection through a particular endpoint, and monitors network traffic and system logs to and from a particular device.
The best intrusion detection systems are built to collect network traffic from all devices via NIDS and HIDS, thus increasing the chances of intrusion detection across your IT infrastructure.
Signature Detection: Signature-based IDS solutions use fingerprints of known threats to identify them. Once malware or other malicious content has been identified, a signature is [2] generated and added to the list used by the IDS solution to test incoming content. This enables an IDS to achieve a high threat detection rate with no false positives because all alerts are generated based upon detection of known-malicious content. However, a signature-based IDS is limited to detecting known threats and is blind to zero-day vulnerabilities.
Anomaly Detection: Anomaly-based IDS solutions build a model of the “normal” behavior of the protected system. All future behavior is compared to this model, and any anomalies are labeled as potential threats and generate alerts. While this approach can detect novel or zero-day threats, the difficulty of building an accurate model of “normal” behavior means that these systems must balance false positives (incorrect alerts) with false negatives (missed detections).
Uses of Intrusion Detection System
IDS solutions excel in monitoring network traffic and detecting anomalous activity. They are placed at strategic locations across a [3] network or on devices themselves to analyze network traffic and recognize signs of a potential attack.
- Monitoring the performance of key firewalls, files, routers, and servers to detect, prevent, and recover from cyberattacks
- Enabling system administrators to organize and understand their relevant operating system audit trails and logs that are often difficult to manage and track
- Providing an easy-to-use interface that allows staff who are not security experts to help with the management of an organization’s systems
- Providing an extensive database of attack signatures that can be used to match and detect known threats
- Providing a quick and effective reporting system when anomalous or malicious activity occurs, which enables the threat to be passed up the stack
- Generating alarms that notify the necessary individuals, such as system administrators and security teams, when a breach occurs
- In some cases, reacting to potentially malicious actors by blocking them and their access to the server or network to prevent them from carrying out any further action
References:
- https://logicalread.com/intrusion-detection-system/
- https://www.checkpoint.com/cyber-hub/network-security/what-is-an-intrusion-detection-system-ids/
- https://www.fortinet.com/resources/cyberglossary/intrusion-detection-system
Cite this article:
Nandhinidwaraka. S (2021) The Methods of Intrusion Detection System, AnaTechMaz, pp. 49