- Home
- Future Technologies
- Future Computing
-
Hardware and Software Tools for Wardriving
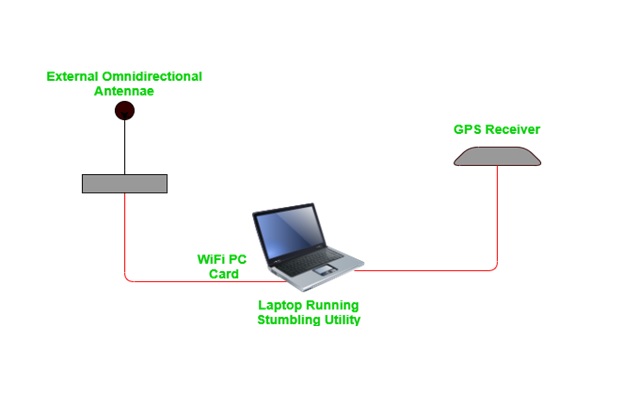
By : Thanusri swetha J, Wardriving consists of physically searching for wireless networks with vulnerabilities from a moving vehicle...
-
Hydrogen Fuel Cells Vehicles
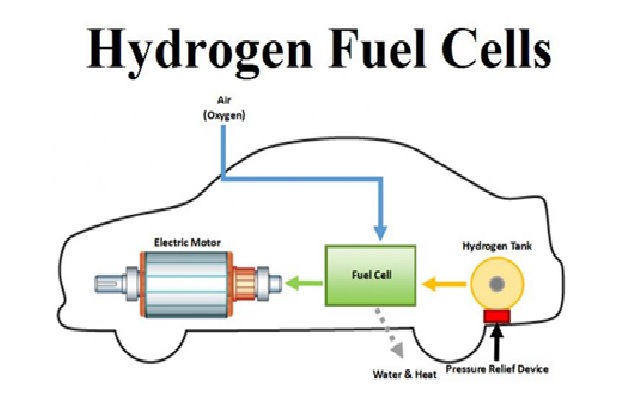
By : Thanusri swetha J, A fuel cell combines hydrogen and oxygen to produce electricity, heat, and water. Fuel cells are often compared to batteries...
-
Importance and Role of Weather Forecasting in Modern Agriculture
By : Thanusri swetha J, Weather forecasting systems use a combination of science and technology...
-
Magnetoresistive Random Access Memory (MRAM)
By : Thanusri swetha J, MRAM (Magnetic RAM) is a memory technology that uses electron spin to store information (an MRAM device is a Spintronics device)...
-
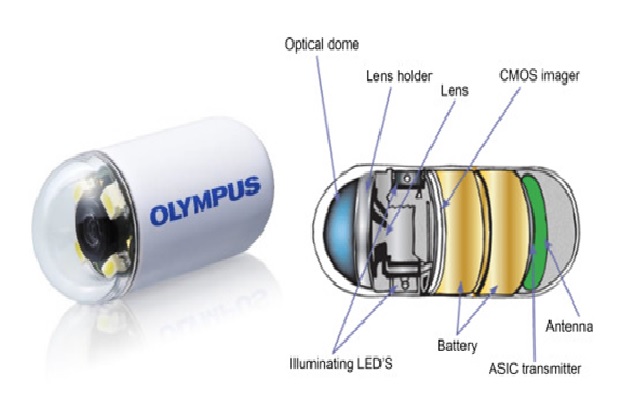
Micro Electronic Pills
By : Thanusri swetha J, Electronic Pill is a tiny capsule-sized electronic device that with the help of various components encapsulated in a small pill helps doctors...
-
Overview of Bluejacking Attack
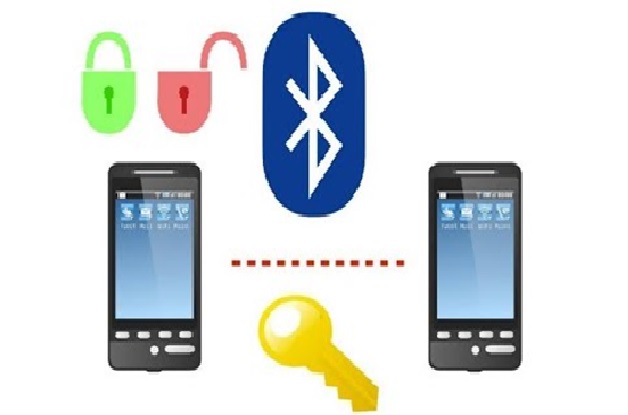
By : Thanusri swetha J, Bluejacking is used for sending unauthorized messages to another Bluetooth device. Bluetooth is a high-speed but very short-range...
-
Overview of Buffer Overflow Attack
By : Thanusri swetha J, A buffer overflow occurs when a program or process attempts to write more data to a fixed-length block of memory, or buffer, than the buffer...
-
Overview of Capsule Endoscopy
By : Thanusri swetha J, Capsule endoscopy is a procedure that uses a tiny wireless camera to take pictures of your digestive tract. A capsule...
-
Overview of Gesture Recognition Technology
By : Thanusri swetha J, Gesture recognition is a type of perceptual computing user interface that allows computers to capture and interpret human gestures...
-
Overview of iontophoresis
By : Thanusri swetha J, Iontophoresis is the process of passing a weak electrical current through the skin. Iontophoresis has a variety of uses in medicine...
-
Overview of MEMS (Micro Electro Mechanical System)
By : Thanusri swetha J, A MEMS (micro-electromechanical system) is a miniature machine that has both mechanical and electronic components...
-
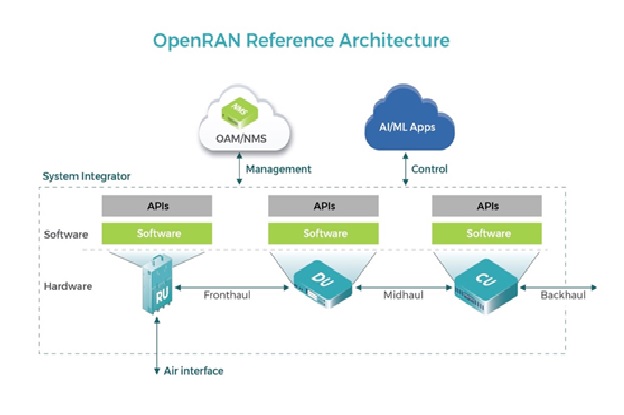
Overview of OpenRAN Reference Architecture
By : Thanusri swetha J, Open RAN is a collaboration of equipment makers and telecoms in various working groups to solve this interoperability problem...
-
Overview of Paper Battery
By : Thanusri swetha J, A paper battery is a thin, flexible energy production and storage device that is formed by combining carbon nanotubes...
-
Overview of Software Reuse
By : Thanusri swetha J, Software reuse is the process of implementing or updating software systems using existing software assets. The systematic...
-
Overview of Steganography
By : Thanusri swetha J, Steganography is the technique of hiding secret data within an ordinary, non-secret, file or message in order to avoid detection...