Quantum-Enhanced Encryption
A method for video encryption and decryption on quantum computers is proposed based on color information transformations on each frame encoding the content of the encoding the content of the video. The proposed method provides a flexible operation to encrypt quantum video by means of the quantum measurement in order to enhance the security of the video. To validate the proposed approach, a tetris tile-matching puzzle game video is utilized in the experimental simulations. The results obtained suggest that the proposed method enhances the security and speed of quantum video encryption and decryption, both properties required for secure transmission and sharing of video content in quantum communication.[1]

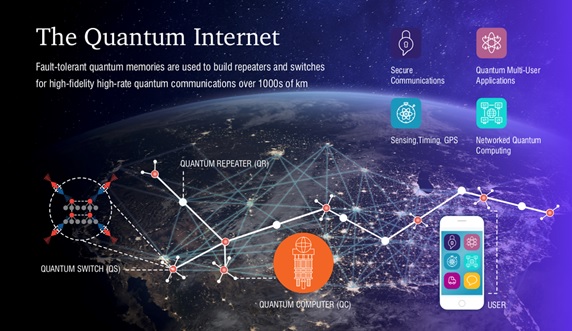
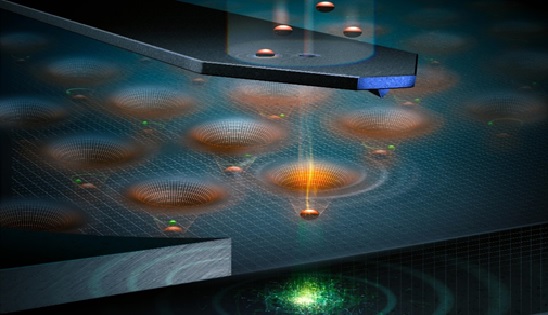
Figure 1. The Quantum – Enhanced Encryption
Figure 1 shows Quantum cryptography is a technology that uses quantum physics to secure the distribution of symmetric encryption keys. A more accurate name for it is quantum key distribution (QKD). It works by sending photons, which are “quantum particles” of light, across an optical link.
The principles of quantum physics stipulate that observation of a quantum state causes perturbation. The various QKD protocols are designed to ensure that any attempt by an eavesdropper to observe the transmitted photons will indeed perturb the transmission.
This perturbation will lead to transmission errors, which can be detected by the legitimate users. This is used to verify the security of the distributed keys.[2]
Quantum Cryptography Works
Quantum cryptography, or quantum key distribution (QKD), uses a series of photons (light particles) to transmit data from one location to another over a fiber optic cable. By comparing measurements of the properties of a fraction of these photons, the two endpoints can determine what the key is and if it is safe to use.
Breaking the process down further helps to explain it better.
The sender transmits photons through a filter (or polarizer) which randomly gives them one of four possible polarizations and bit designations: Vertical (One bit), Horizontal (Zero bit), 45 degree right (One bit), or 45 degree left (Zero bit).
The photons travel to a receiver, which uses two beam splitters (horizontal/vertical and diagonal) to “read” the polarization of each photon. The receiver does not know which beam splitter to use for each photon and has to guess which one to use.
Once the stream of photons has been sent, the receiver tells the sender which beam splitter was used for each of the photons in the sequence they were sent, and the sender compares that information with the sequence of polarizers used to send the key. The photons that were read using the wrong beam splitter are discarded, and the resulting sequence of bits becomes the key.
If the photon is read or copied in any way by an eavesdropper, the photon’s state will change. The change will be detected by the endpoints. In other words, this means you cannot read the photon and forward it on or make a copy of it without being detected.[3]
Difference between post-quantum cryptography and quantum cryptography
Post-quantum cryptography refers to cryptographic algorithms (usually public-key algorithms) that are thought to be secure against an attack by a quantum computer. These complex mathematical equations take traditional computers months or even years to break. However, quantum computers running Shor’s algorithm will be able to break math-based systems in moments.
Quantum cryptography, on the other hand, uses the principles of quantum mechanics to send secure messages, and unlike mathematical encryption, is truly un-hackable.[3]
References:
- https://www.researchgate.net/publication/272168056_Video_Encryption_and_Decryption_on_Quantum_Computers
- https://www.idquantique.com/quantum-safe-security/overview/quantum-key-distribution/
- https://quantumxc.com/blog/quantum-cryptography-explained/
Cite this article:
Thanusri swetha J (2021), Quantum Enhanced Encryption, AnaTechMaz, pp.17