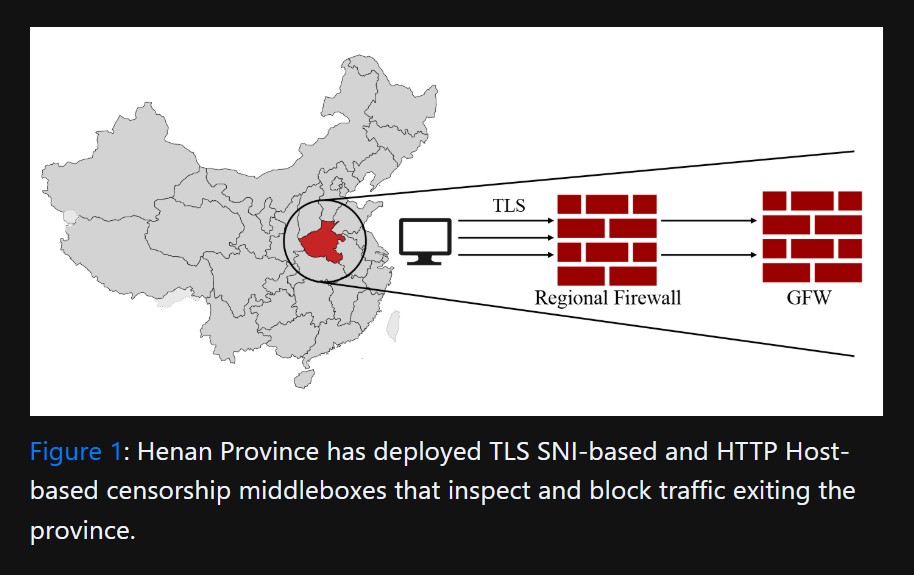
Police Dismantle 300 Servers in Major Ransomware Supply Chain Crackdown
In the latest phase of Operation Endgame, a coordinated international law enforcement effort, authorities from seven countries have seized 300 servers and 650 domains that were instrumental in launching ransomware attacks.
Between May 19 and 22, law enforcement agencies dismantled these infrastructures, issued international arrest warrants for 20 suspects, and seized €3.5 million in cryptocurrency, bringing the total amount confiscated during the operation to €21.2 million, according to the operation's official statement.

Figure 1. Police Dismantle 300 Servers.
Working in collaboration with private sector partners, Europol and Eurojust led the operation, targeting several prominent malware campaigns, including Bumblebee, Lactrodectus, Qakbot, DanaBot, Trickbot, and Warmcookie. These malware tools are commonly used in malware-as-a-service schemes, giving other cybercriminals access to victim networks and enabling ransomware attacks.
“This phase proves law enforcement's agility in adapting and striking back, even as cybercriminals evolve,” said Catherine De Bolle, Executive Director of Europol. “By dismantling the services that cybercriminals rely on, we're disrupting the ransomware deployment chain at its core. “Figure 1 shows Police Dismantle 300 Servers.
DanaBot Charges Unsealed
The U.S. Department of Justice also announced charges against 16 members of a Russian cybercrime group behind the DanaBot malware operation. Of the 16, eight have been named publicly, while the others are identified by their aliases.
According to the charges, the group used DanaBot to deploy additional malware, including ransomware, infecting more than 300,000 systems globally and causing over $50 million in damages. Operating since 2018, DanaBot functions as a subscription-based service, providing clients with access to its botnet, tools, and remote capabilities. It can hijack banking sessions, steal user data and browsing history, and even enable keystroke logging and screen recording.
Authorities also revealed that a second version of DanaBot was used for cyberespionage, targeting sensitive organizations such as military, diplomatic, and government entities in North America and Europe. This variant sent stolen data to a separate server and recorded all user interactions.
Ongoing Efforts Under Operation Endgame
This week's actions build on prior phases of Operation Endgame, which included the seizure of over 100 servers and more than 2,000 domains linked to various malware loaders like IcedID, Pikabot, Bumblebee, Trickbot, Smokeloader, and SystemBC.
Earlier efforts also led to:
- The June 2024 arrest of a Conti and LockBit ransomware crypter developer, who helped malware evade antivirus detection.
- The April takedown of Smokeloader customers, using intelligence from a seized database containing subscriber details.
- The indictment of Rustam Rafailevich Gallyamov, a Russian national alleged to be the mastermind behind the Qakbot operation, which infected over 700,000 devices.
In a Microsoft-led operation earlier this month, law enforcement also seized around 2,300 domains used by the Lumma MaaS info-stealer network, further weakening cybercriminal infrastructure.
Reference:
- https://www.bleepingcomputer.com/news/security/police-takes-down-300-servers-in-ransomware-supply-chain-crackdown/
Cite this article:
Keerthana S (2025), Police Dismantle 300 Servers in Major Ransomware Supply Chain Crackdown, AnaTechMaz, pp.175