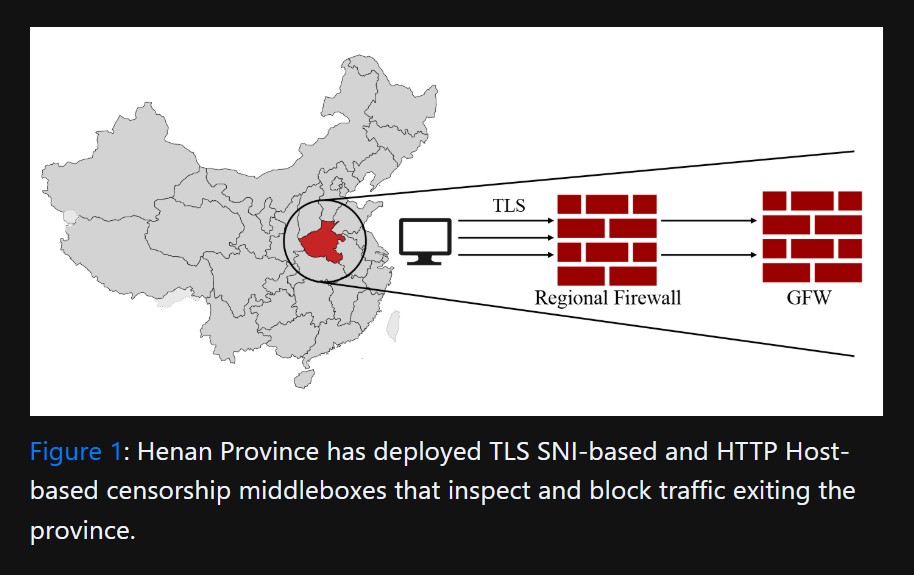
Intel Memory Leak Opens Door for Hackers to Steal Data Rapidly
Researchers at ETH Zurich have discovered a critical vulnerability in Intel processors that allows attackers to steal sensitive data by exploiting the way modern CPUs predict future operations. By crafting specific instruction sequences, attackers can bypass security barriers and slowly access the full memory of a shared processor. This flaw impacts many Intel chips found in personal computers, laptops, and cloud servers.
Researchers have uncovered a new type of vulnerability in Intel CPUs related to speculative execution—a method processors use to speed up performance by predicting upcoming instructions. This flaw enables attackers to bypass isolation between users on the same processor, potentially gaining access to private data stored in memory. By rapidly repeating the attack, hackers can gradually extract memory content one byte at a time until the entire data is exposed. The vulnerability impacts all Intel processors released over the past six years, spanning devices from personal computers to large-scale data center servers. This finding underscores the increasing security challenges associated with performance-enhancing features in modern chip architecture.

Figure 1. ETH Zurich Finds Intel CPU Flaw Exploiting Nanosecond Timing Glitch
Prediction Technology: The Hidden Price of Speed
Anticipating future events gives us an advantage in daily life—and computers use a similar strategy. Modern processors rely on speculative execution, a feature that predicts and runs likely upcoming instructions to significantly boost performance. Figure 1 shows ETH Zurich Finds Intel CPU Flaw Exploiting Nanosecond Timing Glitch.
However, a new breakthrough from ETH Zurich’s Computer Security Group exposes a serious drawback. Researchers have identified a class of vulnerabilities that can exploit the CPU’s prediction engine. By sending specially designed instruction sequences, attackers can bypass security barriers and gain access to data from other users.
Broad Impact on Intel Processors
“The security flaw affects all Intel processors,” states Kaveh Razavi, head of COMSEC. “This vulnerability enables us to read the entire contents of another user’s processor buffer memory (cache) and working memory (RAM) on the same CPU.” The CPU relies on RAM and cache to temporarily store calculations and data likely to be needed next.
The security risks are especially severe in cloud environments, where multiple users share hardware resources. From personal laptops to large-scale data center servers, Intel processors worldwide require enhanced protections to safeguard sensitive information.
The Nanosecond Window
Known as Branch Predictor Race Conditions (BPRC), this vulnerability arises during a few-nanosecond window when the CPU switches prediction calculations between users with different permission levels, explains researcher Sandro Rüegge. The breach occurs because permission data for individual tasks isn’t stored simultaneously with the calculations. By using specific inputs, attackers can cause ambiguity in the user-switching sequence, leading to incorrect privilege assignments and enabling them to read individual bytes of information.
From Single Bytes to Full Memory Access
While reading a single byte might seem minor, the attack can be repeated rapidly, allowing the entire memory content to be extracted over time. “We can trigger the flaw repeatedly and reach read speeds exceeding 5,000 bytes per second,” says Rüegge. Thus, given enough time, an attacker can access all the data in the CPU’s memory.
A Continuing History of CPU Vulnerabilities
This vulnerability is not the first related to speculative execution, a performance feature introduced in the mid-1990s. The well-known Spectre and Meltdown flaws surfaced in 2017, and new variants have emerged regularly since. In 2022, Johannes Wikner, a former PhD student in Razavi’s group, discovered Retbleed—a flaw exploiting traces of speculatively executed instructions in the CPU’s cache to access other users’ data.
Clues Hidden in the Cache
The discovery of this new vulnerability built on investigations into Retbleed. Wikner analyzed Intel’s protective measures for Retbleed and detected an unusual signal from the cache memory that appeared regardless of whether protections were active. Sandro Rüegge then conducted an in-depth analysis, which led to uncovering this new attack vector.
A Fundamental Architectural Issue
Discovered in September 2024, Intel has since introduced microcode updates to mitigate the issue. However, Razavi warns the problem is deeper than a single vulnerability. “The ongoing stream of new speculative execution flaws points to fundamental architectural weaknesses,” he says. “Each gap must be identified and patched individually.” Fixes require processor microcode updates, typically delivered through BIOS or operating system updates, so users should ensure their systems are fully up to date with the latest cumulative Windows patches.
References:
- https://scitechdaily.com/intels-memory-leak-nightmare-5000-bytes-per-second-in-the-hands-of-hackers/
Cite this article:
Janani R (2025), Intel Memory Leak Opens Door for Hackers to Steal Data Rapidly, AnaTechMaz, pp. 168