Cybersecurity Mesh
Cybersecurity mesh is a flexible, composable architecture that integrates widely distributed and disparate security services. Cybersecurity mesh enables best-of-breed, stand-alone security solutions to work together to improve overall security while moving control points closer to the assets they’re designed to protect. It can quickly and reliably verify identity, context and policy adherence across cloud and non cloud environments.
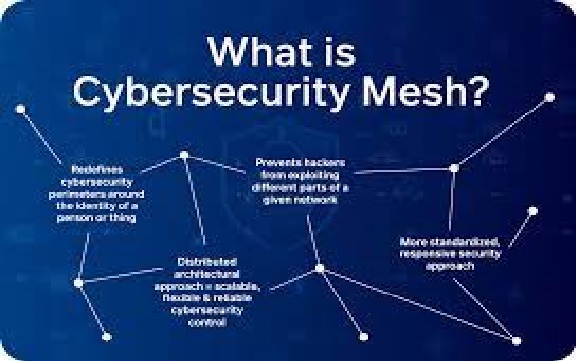
Figure. 1. Cybersecurity Mesh
The mesh ensures that all data, systems, and equipment are treated equally and securely — it doesn’t matter where they are located in (or out) of the network. Any connection to access data is by default considered “unreliable” until it is verified by the security protocol.
Benefits of Cybersecurity Mesh
- Cybersecurity mesh will support majority of Identity and Access Management Requests (IAM)
- Rise in managed security service providers (MSSPs)
- Identity proofing tools in the workforce identity life cycle
- Emergence of Decentralized identity standards
- Reducing Demographic bias within identity proofing
Common Types Of Cyber-Attacks
- Ransomware Attacks
- Iot Attacks
- Cloud Attacks
- Phishing Attacks
- Blockchain And Cryptocurrency Attacks
References:
- https://www.gartner.com/en/information-technology/insights/top-technology-trends
- https://www.simplilearn.com/cybersecurity-mesh article#:~:text=The%20cybersecurity%20mesh%20is%20a%20key%20component%20of%20a%20zero,inside%20of%20the%20network%20itself.
- https://10xds.com/blog/what-is-cybersecurity-mesh/
- https://www.jigsawacademy.com/blogs/cyber-security/challenges-of-cyber-security/
Cite this article:
Sindhu.C (2022), Cybersecurity Mesh Anatechmaz, p.p 72