Unveiling Pathfinder: Advanced Attacks Exploiting Conditional Branch Predictors
Researchers have uncovered two new types of attacks aimed at the conditional branch predictor present in advanced Intel processors, posing a threat to billions of currently deployed processors. Led by computer scientists at the University of California San Diego, a collaborative team from multiple universities and industry partners will present their findings at the 2024 ACM ASPLOS Conference beginning tomorrow. Titled "Pathfinder: High-Resolution Control-Flow Attacks Exploiting the Conditional Branch Predictor," [1] their paper reveals insights from researchers at UC San Diego, Purdue University, Georgia Tech, the University of North Carolina Chapel Hill, and Google.
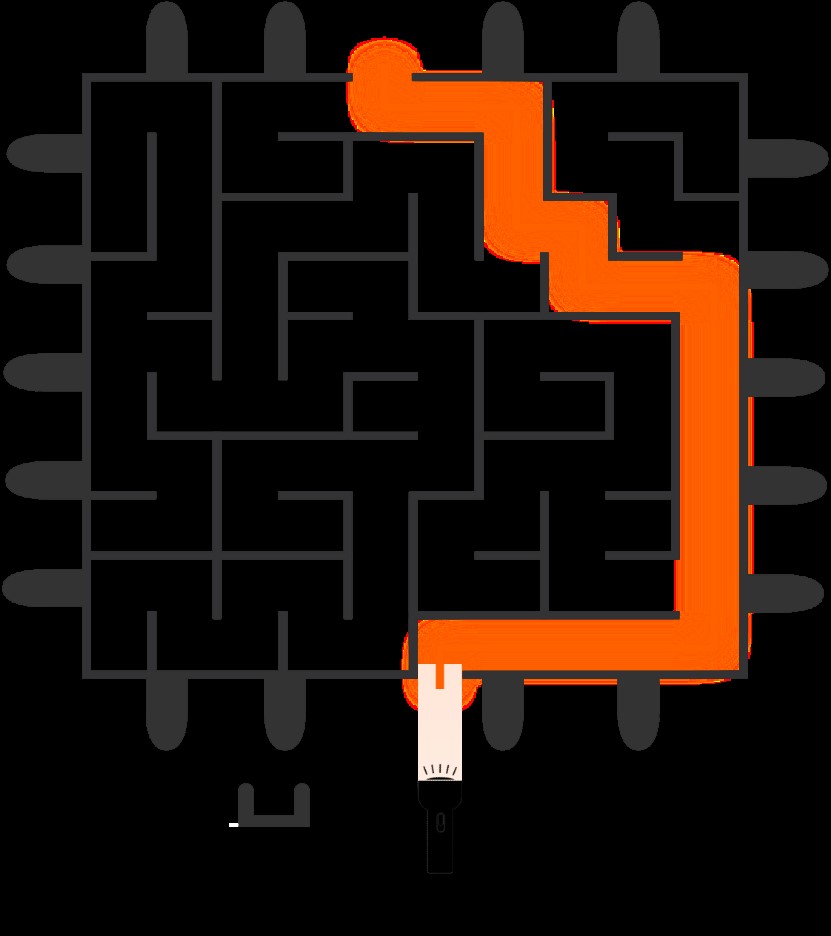
Figure 1. Pathfinder. (Credit: University of California - San Diego)
Figure 1 is an illustration of Pathfinder. One novel attack targets the Path History Register (PHR), a feature within the branch predictor that monitors both branch order and addresses. Unlike previous attacks, this approach offers finer precision by tapping into the exact structure of the branch predictor, exposing more detailed information.
Intel and Advanced Micro Devices (AMD) have responded to the concerns raised by the researchers by addressing the security issues and informing users. Intel is expected to issue a Security Announcement today, while AMD will release a Security Bulletin. [2]
In modern software, frequent branching occurs as programs follow different paths based on varying data values. Optimizing processor performance, the branch predictor anticipates future branch outcomes by referencing past histories stored within prediction tables. Previous attacks analyzed these tables to discern recent branch tendencies at specific addresses.
The new study focuses on leveraging the Path History Register (PHR) used by modern predictors to index prediction tables. This register records the addresses and order of the last 194 taken branches in recent Intel architectures. With innovative techniques, the researchers demonstrate the ability to capture not only recent outcomes but also every branch outcome in sequential order, revealing the global ordering of all branches.
"We successfully captured sequences of tens of thousands of branches in precise order, utilizing this method to leak secret images during processing by the widely used image library, libjpeg,” said Hosein Yavarzadeh, a UC San Diego Computer Science and Engineering Department PhD student and lead author of the paper. [2]
The team also introduces a highly precise Spectre-style poisoning attack, allowing attackers to induce intricate patterns of branch mispredictions within victim code, leading to the execution of unintended code paths and exposing confidential data.
"While prior attacks could misdirect a single branch or the first instance of a branch executed multiple times, we now have such precise control that we could misdirect the 732nd instance of a branch taken thousands of times,” said UC San Diego computer science Professor Dean Tullsen. [1]
Their proof-of-concept demonstrates forcing an encryption algorithm to transiently exit earlier, thereby exposing reduced-round ciphertext and illustrating the ability to extract the secret AES encryption key.
"Pathfinder can reveal the outcome of almost any branch in almost any victim program, making it the most precise and powerful microarchitectural control-flow extraction attack that we have seen so far," said Kazem Taram, an assistant professor of computer science at Purdue University and a UC San Diego computer science PhD graduate. [3]
In addition to Dean Tullsen and Hosein Yavarzadeh, other UC San Diego coauthors are Archit Agarwal and Deian Stefan. Coauthors from other institutions include Christina Garman and Kazem Taram from Purdue University, Daniel Moghimi from Google, Daniel Genkin from Georgia Tech, and Max Christman and Andrew Kwong from the University of North Carolina Chapel Hill.
This research received support from various sources including the Air Force Office of Scientific Research (FA9550-20-1-0425), the Defense Advanced Research Projects Agency (W912CG-23-C-0022 and HR00112390029), the National Science Foundation (CNS-2155235, CNS-1954712, and CAREER CNS-2048262), the Alfred P. Sloan Research Fellowship, and gifts from Intel, Qualcomm, and Cisco.
Source: University of California - San Diego
References:
- https://www.eurekalert.org/news-releases/1042769
- https://www.eurasiareview.com/27042024-computer-scientists-unveil-novel-attacks-on-cybersecurity/
- https://www.sciencedaily.com/releases/2024/04/240426165229.htm
Cite this article:
Hana M (2024), Unveiling Pathfinder: Advanced Attacks Exploiting Conditional Branch Predictors, AnaTechMaz, pp. 256