Biometrics in Secure e-Transaction
Biometrics in Secure e-Transaction
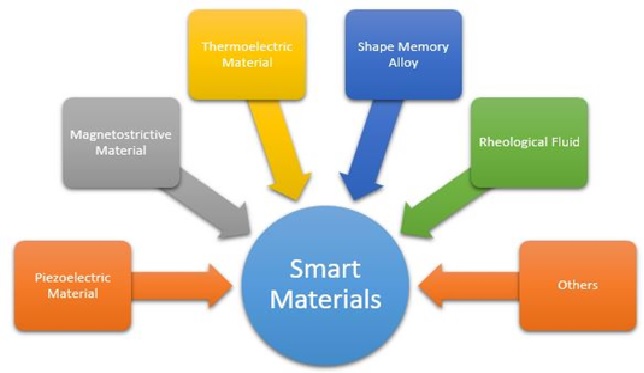
In the present day word, online shopping using WAP enabled mobile phone has widely come into use. Credit cards serve as the currency during e-business and e-Shopping. As technology has advanced in the negative side also hackers steal, misuse credit card numbers, even though the network has been made secure. So, in this paper, the authors have proposed a multi-biometric model (integrating voice, fingerprint and facial scanning) that can be embedded in a mobile phone, this making e-transactions more secure. [1]

Figure. 1. Biometrics in Secure e-Transaction
MULTIBIOMETRICS
A multi-biometrics system is obtained by the integration of multiple individual biometrics models. A numbers of models integrating hand geometry, keystroke dynamics, face and iris recognition system have flooded the markets in recent years. Here we present a multimodal system that can be embedded in a mobile phone, which integrates fingerprint, voice and facial scanning. It shuts down the problem of high False Rejection Rate of facial scanners, eliminates the fooling of fingerprint scanners and overshadows the disadvantage of voice recognition models. Multi-biometric systems use multiple sensors or biometrics to overcome the limitations of unimodal biometric systems.For instance iris recognition systems can be compromised by aging iris and finger scanning systems by worn-out or cut fingerprints. While unimodal biometric systems are limited by the integrity of their identifier, sequential, parallel, hierarchical and serial integration modes, respectively. Broadly, the information fusion is divided into three parts
- pre-mapping fusion
- midst-mapping fusion
- and post-mapping fusion/late fusion.
- Single sensor-multiple instances
- intra-class multiple sensors
- Inter-class multiple sensors.
- intra-class
- Inter-class.
- Same sensor-same features
- Same sensor-different features
- Different sensors-same features
- Different sensors-different features
NEED FOR BIOMETRICS IN MOBILE PHONES:
Nowadays, shopping through the internet has become very popular and surely, a WAP enabled mobile phone provides the facilities to consumers to shop online. Credit cards continue to be an efficient tool for online money transactions. But, on the other hand, credit card's number can be stolen on its way to its destination and can be misused by hackers. Thus, e-Business through a mobile phone becomes insecure. Also anti-fraud Software, like those provided by ArticSoft and ISC, created a back door entry and were largely involved in data spoofing. In addition to this, many user and companies were prone to the attack of many viruses and Trojan horses. With so much of problems faced, the service provide turned their attention towards biometrics to prevent data spoofing and to provide secure e-Transactions
References:
- https://www.techrepublic.com/resource-library/whitepapers/biometrics-in-secure-e-transaction/
- https://www.ijettcs.org/Volume2Issue2/IJETTCS-2013-04-25-181.pdf
- https://www.seminarsonly.com/computer%20science/BIOMETRICS-in-SECURE-E-transactions.php
Cite this article:
Nithyasri S (2022), Biometrics in Secure e-Transaction, AnaTechMaz, pp. 84